Ledger Live Login: A Complete Guide to Secure Access and Digital Asset Management
In today’s world of digital finance, managing cryptocurrencies safely is a priority for anyone holding digital assets. Ledger Live is one of the most widely used applications for interacting with Ledger hardware wallets, allowing users to manage multiple cryptocurrencies securely in one place. The term Ledger Live Login represents the first step in accessing and controlling your digital assets. Understanding how Ledger Live works, its security measures, and best practices is essential for anyone looking to maintain safe and efficient management of their funds. This article provides a comprehensive guide to Ledger Live Login, explaining the process, security principles, and responsible usage for beginners and advanced users alike.
Understanding Ledger Live
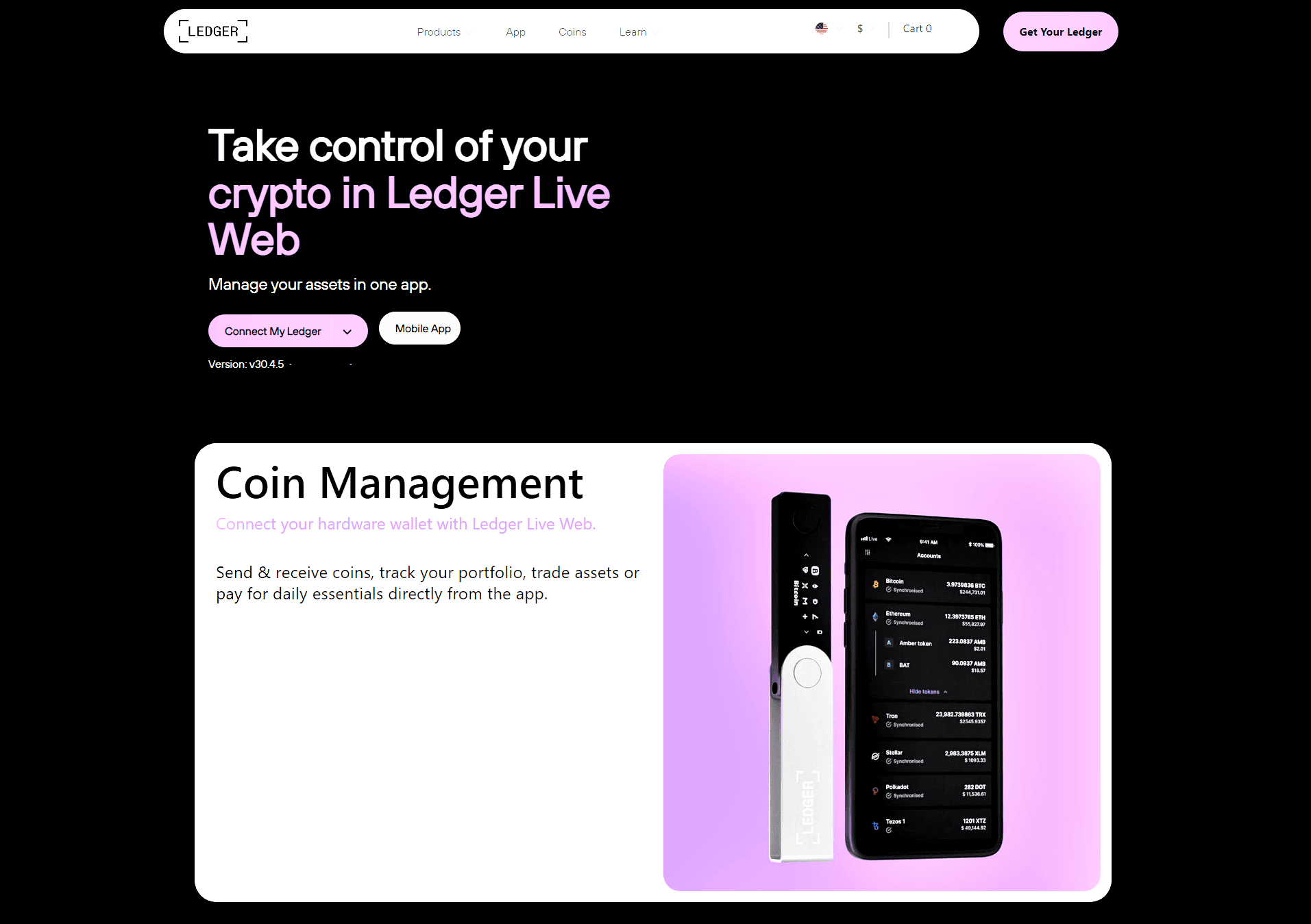
Ledger Live is a desktop and mobile application designed to provide a secure interface between your Ledger hardware wallet and your digital assets. It allows users to send and receive cryptocurrencies, monitor account balances, and manage multiple assets from one centralized interface. Unlike software wallets that store private keys online, Ledger Live works in conjunction with the Ledger hardware wallet to maintain the security of your keys offline.
Ledger Live is compatible with numerous cryptocurrencies and tokens, supporting a wide range of digital assets. Its integration with Ledger hardware wallets ensures that private keys never leave the device, allowing transactions to be signed securely offline. The application also provides updates, notifications, and analytics to help users stay informed about their holdings.
The Importance of Secure Login
The Ledger Live Login is the gateway to accessing and managing your digital assets. Unlike traditional online accounts, access to Ledger Live does not rely on usernames and passwords alone. The security of Ledger Live hinges on the hardware wallet, the recovery phrase, and additional authentication measures. Understanding these components is critical for protecting assets against unauthorized access, theft, and loss.
Steps to Access Ledger Live
Accessing Ledger Live requires a combination of software and hardware interaction. While the specific process may vary slightly depending on device and operating system, the general steps include:
Install the Ledger Live Application: Users download and install the official Ledger Live software from a verified source. Ensuring the authenticity of the software prevents exposure to malicious programs or fake applications.
Connect Your Ledger Device: The hardware wallet is connected to the computer or mobile device via USB or Bluetooth, depending on the model. Ledger Live recognizes the device and establishes a secure connection.
Unlock the Device: The Ledger hardware wallet is unlocked using a PIN code. This PIN is unique to each device and prevents unauthorized access to its contents.
Open Ledger Live: The user launches the Ledger Live application and follows the prompts to connect the device. Ledger Live synchronizes with the blockchain to display account balances and transaction history.
Authenticate Transactions: When sending or receiving assets, Ledger Live interacts with the hardware wallet to sign transactions securely. The private keys never leave the device, maintaining offline security.
By following these steps, users can securely access and manage their digital assets through Ledger Live without compromising security.
Security Principles Behind Ledger Live
Ledger Live operates on the principle of secure access through hardware authentication. Unlike online wallets, where private keys may be exposed to the internet, Ledger Live relies on the hardware wallet to store keys offline. This approach ensures that even if the computer or mobile device is compromised, the cryptographic keys remain secure.
Several security principles are central to Ledger Live Login:
Hardware-Based Authentication: The hardware wallet serves as a secure environment for storing private keys and signing transactions. Access is only granted through physical confirmation on the device.
PIN Protection: Each hardware wallet requires a PIN to unlock the device, preventing unauthorized physical access.
Recovery Phrase Backup: The recovery phrase acts as a master key, allowing users to restore access to their assets if the device is lost or damaged. Proper storage and security of this phrase are essential.
Encrypted Communication: Ledger Live communicates with the hardware wallet using encrypted channels, ensuring that sensitive information is protected during transmission.
Transaction Verification: Users confirm all transactions directly on the hardware wallet, reducing the risk of malware or software manipulation.
Managing Multiple Assets
One of the advantages of Ledger Live is the ability to manage multiple cryptocurrencies from one interface. Users can create separate accounts for different assets, view balances, and track transaction history. The software also provides portfolio analytics, showing overall asset distribution, performance, and trends.
Ledger Live supports major cryptocurrencies such as Bitcoin, Ethereum, and Litecoin, as well as numerous tokens. Regular updates ensure compatibility with new assets and emerging blockchain networks. This multi-asset support allows users to maintain comprehensive control over their holdings without relying on multiple wallets or platforms.
The Role of Updates and Firmware
Ledger Live provides regular updates for both the software and the hardware wallet firmware. Keeping both updated is critical for security, as updates often include protection against newly discovered vulnerabilities, support for new assets, and improvements to the user experience.
Users are encouraged to verify updates through official channels and avoid installing software from untrusted sources. Firmware updates on the hardware wallet require direct interaction with the device, ensuring that unauthorized software cannot modify its internal operations.
Security Best Practices
To ensure the security of your Ledger Live Login and digital assets, adopting best practices is essential. Key practices include:
Verify Sources: Only download Ledger Live from official websites or trusted platforms. Avoid third-party download links that could host malicious software.
Secure the Recovery Phrase: Store the recovery phrase in a safe, offline location. Never share it with anyone, and avoid digital storage methods that could be compromised.
Enable PIN Protection: Use a strong, unique PIN on your hardware wallet. Avoid using simple sequences that could be easily guessed.
Double-Check Transactions: Always confirm transaction details on the hardware wallet display before signing. Ensure the recipient address and amounts are correct.
Update Regularly: Keep both Ledger Live software and hardware wallet firmware up to date. Updates protect against vulnerabilities and improve functionality.
Physical Security: Protect your hardware wallet from theft, loss, or damage. Consider using a safe or other secure storage method when not in use.
Be Wary of Phishing: Be vigilant against emails, messages, or websites claiming to be Ledger support. Only use verified official channels for support or guidance.
By following these best practices, users can maintain secure access to their assets and minimize risks.
Using Ledger Live Mobile
Ledger Live is also available on mobile devices, providing a convenient interface for managing assets on the go. The mobile app works in conjunction with the hardware wallet, connecting via Bluetooth for supported devices. The same security principles apply, including PIN authentication, hardware signing of transactions, and recovery phrase management.
The mobile interface allows users to view balances, send and receive cryptocurrencies, and monitor portfolio performance. While convenient, mobile users should remain cautious about device security, including using secure networks, avoiding public Wi-Fi for transactions, and keeping their phone protected with strong passwords or biometric authentication.
Education and Awareness
Understanding Ledger Live Login goes beyond simply accessing the application. Users should educate themselves about digital asset management, blockchain principles, and security best practices. This knowledge ensures that they can make informed decisions, avoid scams, and respond appropriately to potential threats.
Beginners should start with conceptual learning, including how private and public keys function, how transactions are authorized, and how to manage recovery phrases securely. With this foundation, users are better equipped to handle practical operations without compromising their assets.
Common Misconceptions
Some users mistakenly believe that Ledger Live or hardware wallets make digital assets completely immune to loss. While they provide strong protection against online threats, they cannot prevent mistakes such as losing the recovery phrase, falling for phishing scams, or entering incorrect transaction details.
Another misconception is that Ledger Live Login relies solely on passwords. In reality, access and security depend on the combination of the hardware wallet, PIN, and recovery phrase. Understanding these components is essential for secure management.
The Bigger Picture
Ledger Live Login represents the entry point to a broader ecosystem of secure digital asset management. It symbolizes both access and responsibility—the user’s ability to control assets safely while remaining vigilant against potential risks. Mastery of Ledger Live, combined with good security habits, allows individuals to confidently participate in decentralized finance and digital asset ecosystems.
Ledger Live empowers users to manage their portfolios, interact with blockchain networks, and maintain control over their wealth. Its integration with Ledger hardware wallets provides a balance between convenience and security, ensuring that private keys remain offline and protected at all times.
Conclusion
Ledger Live Login is more than just accessing an application—it is the gateway to managing your digital assets securely and efficiently. By understanding how Ledger Live works, the role of the hardware wallet, and the importance of recovery phrases, users can maintain safe control over their holdings.
Adopting best practices, staying educated, and remaining vigilant against threats are key to long-term success in digital asset management. Ledger Live provides the tools, but responsible usage ensures security and peace of mind. Whether you are new to cryptocurrencies or an experienced user, mastering Ledger Live Login is a fundamental step toward confident, secure, and empowered management of digital assets.
By following the principles outlined in this guide, users can navigate the digital asset ecosystem with confidence, protecting their investments while leveraging the benefits of decentralized finance. Ledger Live Login is not just a technical process—it represents the start of a secure journey in digital wealth management.